-
To Hacker, Thanks. I learnt so much!
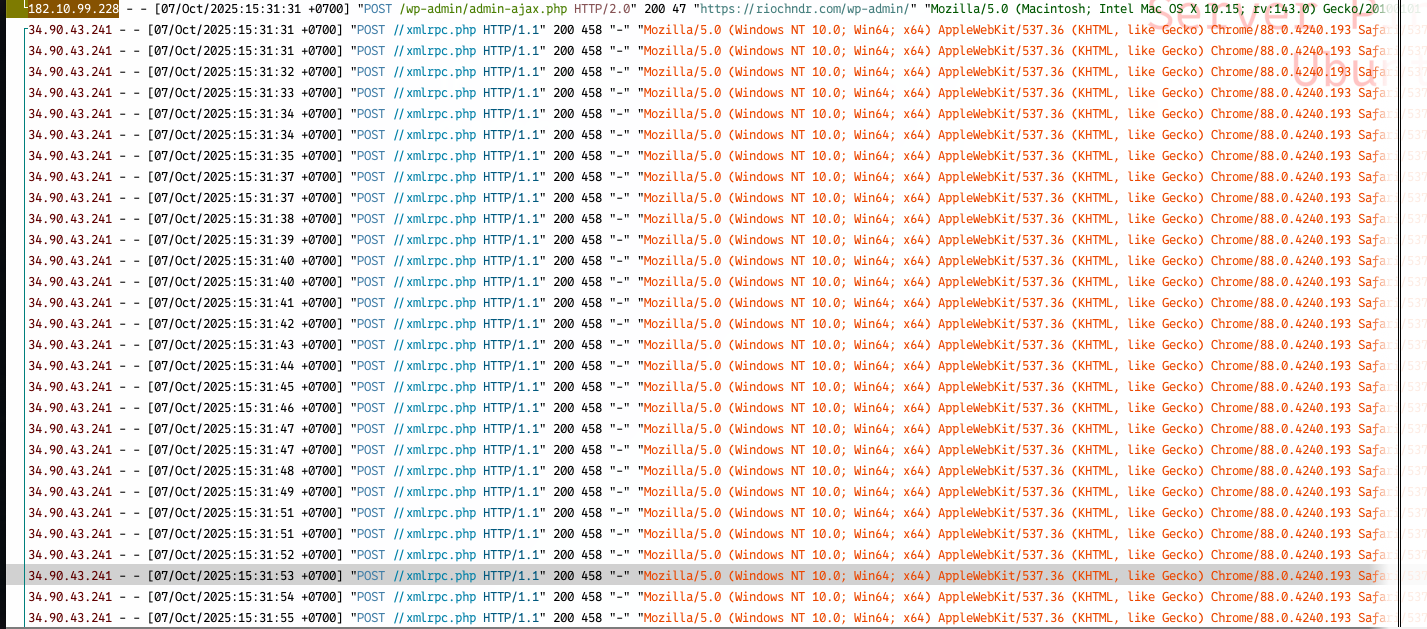
A few days ago my website and server got a lot of traffic without me noticing. Hacker tried brute-force my wordpress blog, it’s small blog what you can expect? or just for fun?. Fortunately they can’t hack it. Here is my story and my lesson that I get. Brute force xmlrpc They are Bruteforcing xmlrpc.php…
Written by
-
Get it done.
Pekerja muda pasti ingin melakukan pekerjaannya dengan baik, mencari best practice disumber manapun, menggunakan metode dan teori terbaik. Tapi pekerjaan menjadi lebih lama, berorientasi perfeksionis sehingga tidak menyelesaikan apapun. Aku menulis ini karena sebagai programmer kadang menghabiskan waktu berjam-jam untuk riset dan mencari best-practice sehingga lupa untuk mengerjakan hal-hal kecil dalam proyek. Aku sadar bahwa…
Written by

-
How Color Theory Influences Website Design
Landing page is the first page user see. I was wondering how to create beautiful color, shape and how it’s affect intention of creator. My curiosity become larger when I read about Color Theory. Color theory isn’t new theory, it has been researched since year 800-ish. I was wondering how it’s affect website looks. So,…
Written by

-
Frontend Tips: Boost Productivity With This Vite Technique
Vite is the best and blazing fast frontend build tool. It includes all feature for developer to build web application faster, like HMR (Hot Module Replacement), build tools, plugins and build on top Rollup. I was using this tool for a couple years, but I just found some tips to increase productivity. It’s a small…
Written by

-
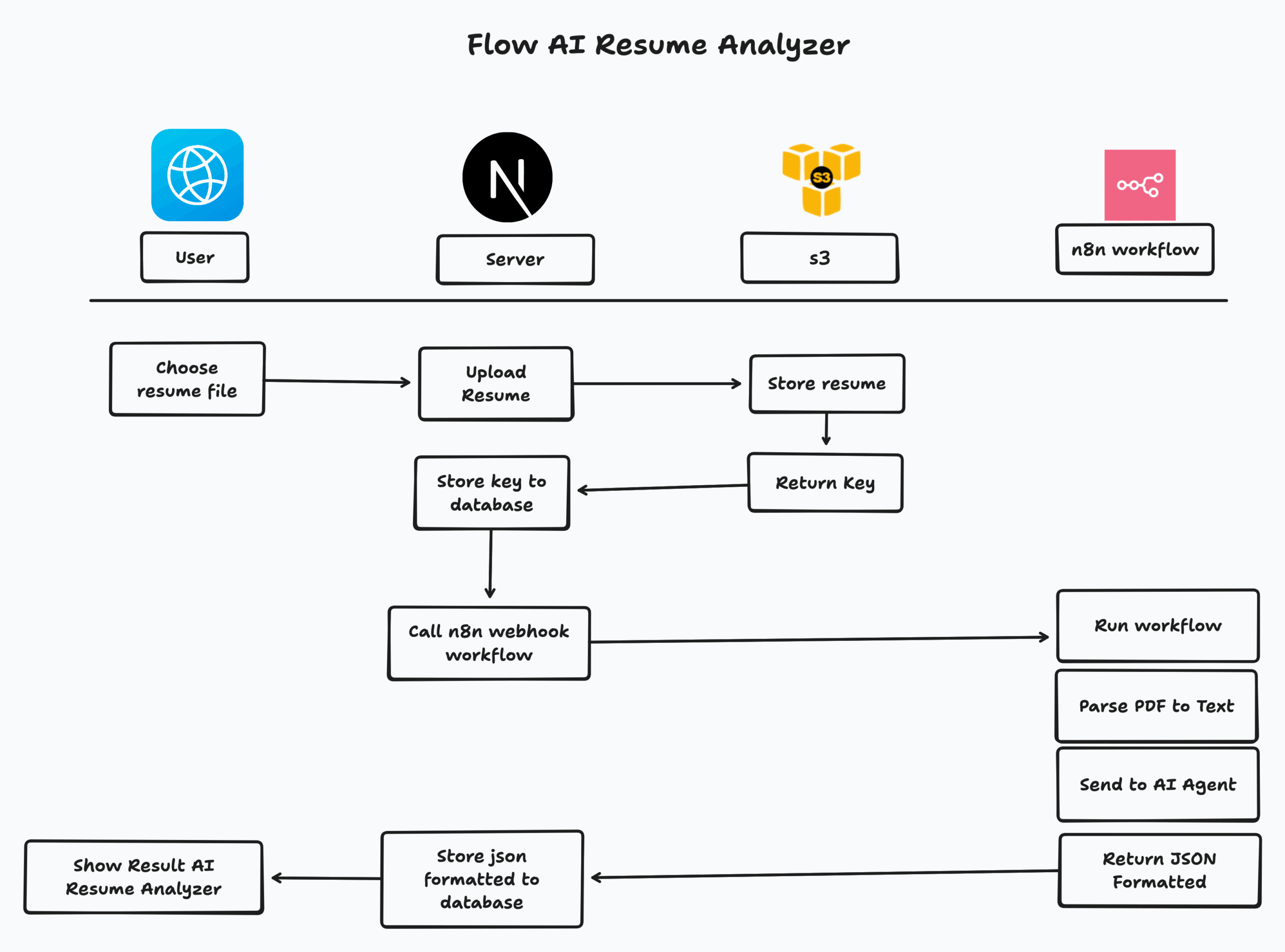
Project Write-Up: Building an AI Resume Parsing with n8n and Next.js
AI become high demanding right now, almost all website and application embed AI in every feature they have. AI or should we called LLM (Large language Model) created by company like openai and gemini gave user access to their LLM using API. This could be exponential usage of AI because we do not require install…
Written by
-
Portfolio Browser — Seamless Transition Image and Text Using GSAP
GSAP really usefull to create animation and transition, I’m inspired by Seamless slider transition. I Try to recreate and add some custom animation like staggered transition image. See the Pen Portfolio Browser by Rio Chandra (@Rio-Chandra) on CodePen. I will not go to detail and explain code-by-code. But I will explain what obstacle I face…
Written by

-
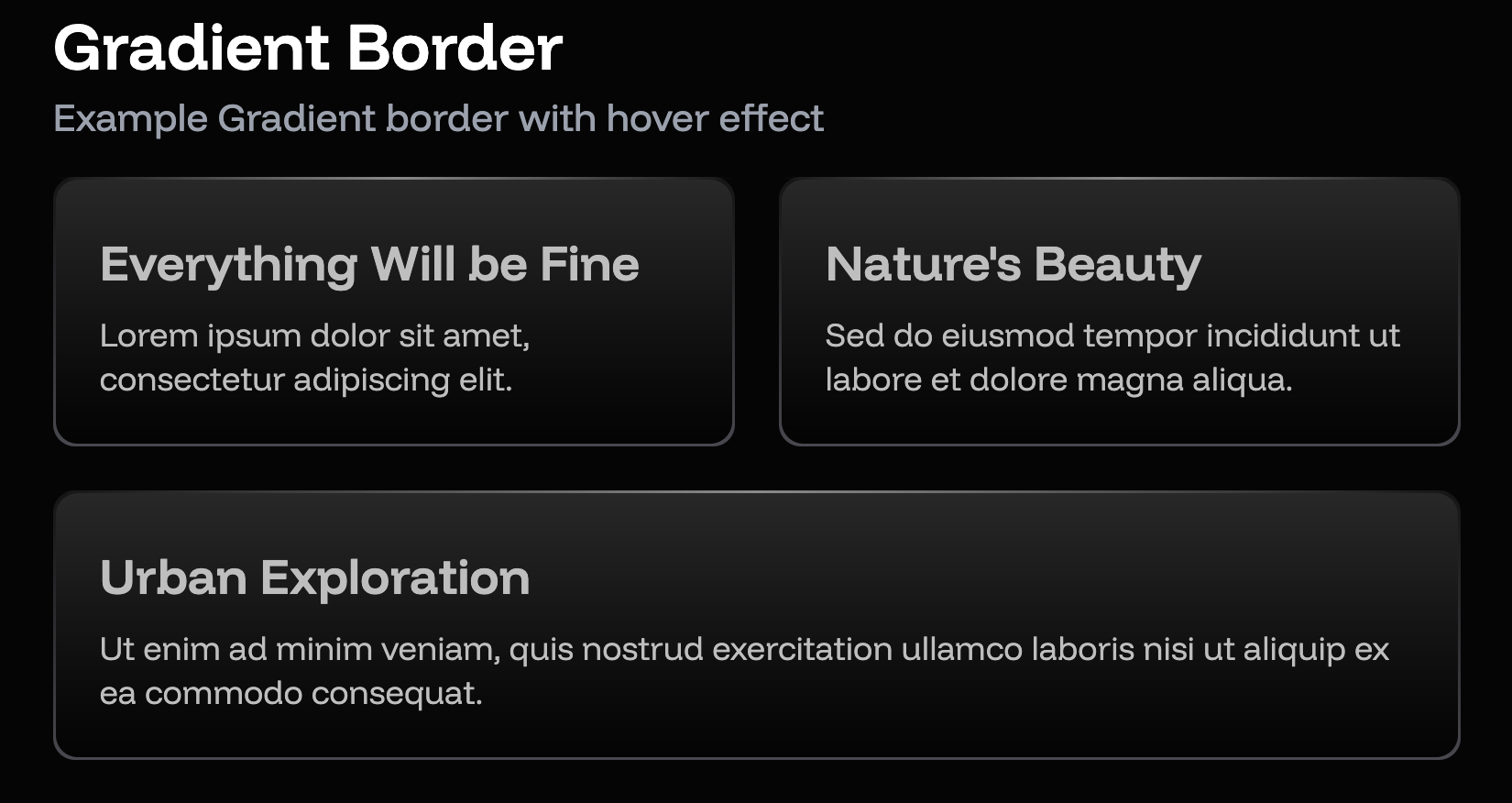
Modern Border Gradient With Tailwindcss
Border in css is boring just because can’t be gradient. Developer do much thing to make it not boring, codyhouse, digitalocean and community dev. But it have trade-off, the border can’t be rounded. Border gradient is modern design when comes to web design, sometimes it mimic how glass works. Let see how we re-create this…
Written by
-
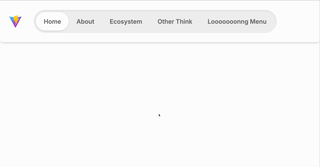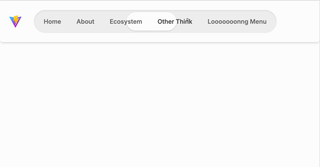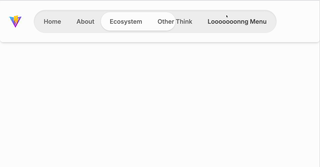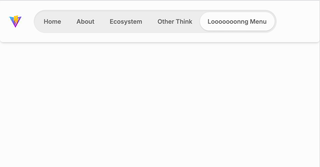
Indicator Navigation Animation: Using GSAP and tailwindcss
Day 1 create navigation indication animation, inspired by this page. I love how moving around the indicator of nav bar. I re-create this using vite, tailwind and gsap. First of all, I create html code And then, these basic structure is enough with nav-indicator as button–moving–thing. and then I add javascript script to make it…
Written by