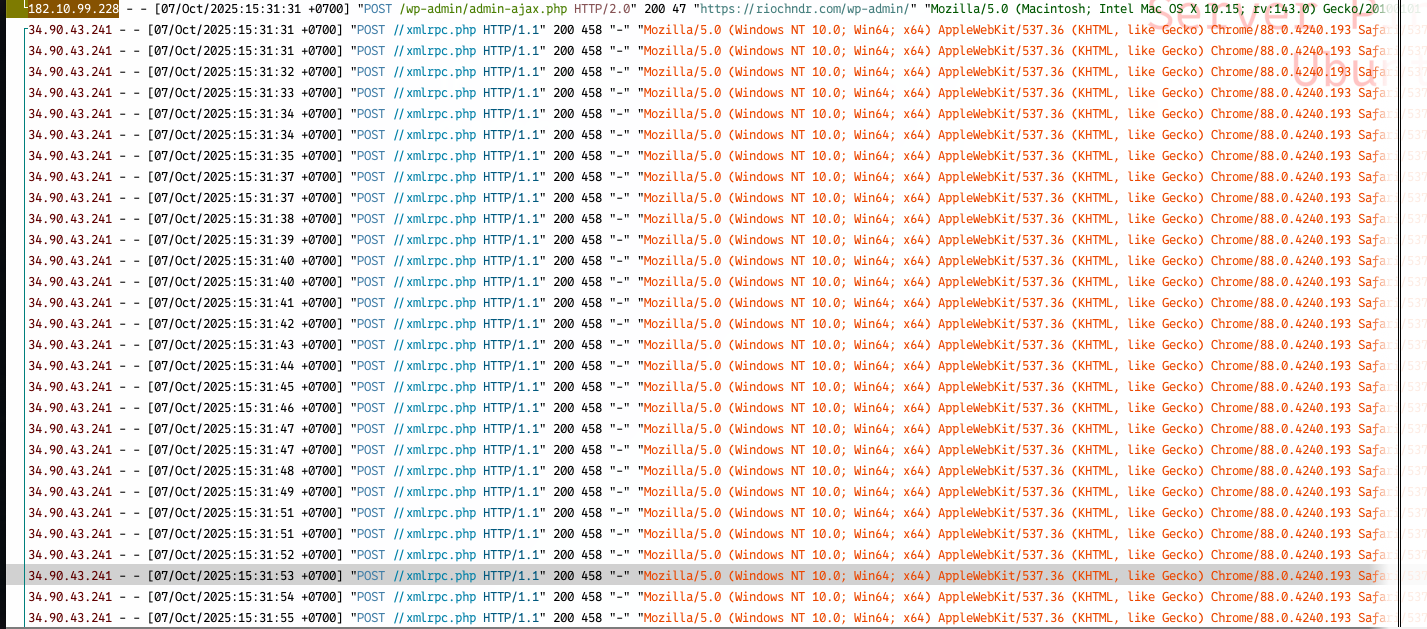
A few days ago my website and server got a lot of traffic without me noticing. Hacker tried brute-force my wordpress blog, it’s small blog what you can expect? or just for fun?. Fortunately they can’t hack it. Here is my story and my lesson that I get.
Brute force xmlrpc
They are Bruteforcing xmlrpc.php which is used by remote application to access wordpress. Thanks to nginx log—I should definetely check on that frequently.

Jetpack application mobile are using xmlrpc.php, but I rarely use it. So, the solution of this problem is block access to this path. Here is configuration nginx to deny all request.
location = /xmlrpc.php {
deny all;
}Even though they are using double slash —//xmlrpc.php. I think this configuration is enough.
Brute force wp-login
Besides that, they are trying other method like wp-login.php. We can’t block this path because used to access wp-admin, but we can add limit request using this configuration in nginx:
limit_req_zone $binary_remote_addr zone=WPRATELIMIT:30m rate=2r/s;
server {
location ~ \wp-login.php$ {
limit_req zone=WPRATELIMIT;
}
}Path Traversal
After couple hours, they are trying access other path or directory outside of intended directories which maybe contain backdoor or malware or insecure code.

Since beginning I always make sure my wordpress as light as possible—remove unused plugin and themes, also update frequently. It’s small action but it have big impact.
Block IPs
Thanks to lnav, I can filter the IP in my log. The first 2 IP is suspicious and abnormal amount of request.

I block these IP with simple configuration, I add include blockips in nginx.conf file, and create new file blockips.conf to store all banned IPs.
# nginx.conf
http {
include blockips.conf;
}
# blockips.conf
deny 167.99.65.122;
deny 167.71.23.155;Now I can block any IP easily with single file.
Conclusion
Digital security is not single action but continous actions, it should be maintained effectively. I can do this because I have access directly to server, so I can pin point where the solution and the problem effectively. If you are taking my advice as your solution, please validate your system server and ask your engineer to do that.
Thank you for your reading. and thanks to hacker for valueable leason.