ENV is a very important part of any application. It is used to store sensitive information in it, like credential, secret key, configuration, and other thing that we put inside it.
Usually env used at application along with other file in the root folder. It SHOULD NEVER put in git history even your repository is private in github or gitlab.
Where to Store ENV
We will use it in server or application configuration on the cloud. If you have budget you can store it at
They have great API and security to store and fetch the key. Those env key should be encrypted to securely store them.
You can do manually by encrypt the file env send them into server, then decrypt inside your server. There is several method to do that. We will use SOPS to encrypt and decrypt them. After encryption you can include encrypted file inside your git history. This is not a problem
What is SOPS
SOPS (Secrets OPerationS) is an editor of encrypted files that supports YAML, JSON, ENV, INI and BINARY formats and encrypts with AWS KMS, GCP KMS, Azure Key Vault, age, and PGP. – SOPS Repository
SOPS is a tool that help us to encrypt file key (YAML, JSON, ENV, INI and BINARY). The key point of this tool is it ONLY encrypt the KEY value only. See their demo here
Ok, lets do this
Installation
If you have brew inside your OS, install using this command
brew install sops
If you using another OS, see SOPS Release Page
Encrypt using GPG
SOPS support many of encryption method like GPG, age, GCP KMS, AWS KMS. We will use GPG for our testing.
Create GPG Key
If you do not have gpg in your system, please install it first
$ brew install gnupg
# Or in linux enviroment
$ sudo apt install gnupg
See GnuPG if you have problem of installation.
Create your key using this command, gpg will ask your email but it not require validation, just remember it for the next step.
gpg --full-generate-key
Fill each form and then press enter.
Get your Public Key GPG
Get your public key using command gpg --list-keys your-email@mail.com
$ gpg --list-keys your-email@mail.com
pub rsa2048 2024-02-26 [SC]
E9FA8C3C96FE003FF38FD7552459B2802BA5CDBF
uid [ultimate] Rio Chandra <riochandra4@gmail.com>
uid [ultimate] [jpeg image of size 5231]
sub rsa2048 2024-02-26 [E]
sub dsa2048 2024-02-27 [S]
The E9FA8C3C96FE003FF38FD7552459B2802BA5CDBF is my public key, it should under pub line.
Create SOPS Configuration
.sops.yaml is file configuration public key for SOPS. Create new file inside your project with name .sops.yaml with following content:
creation_rules:
- pgp: >-
E9FA8C3--CHANGE-WITH-YOUR-PUBLIC-KEY--CDBF
if you have many of public keys, for example first is your key and second is your server’s key, put comma at the end of line public key
# Using multiple key pgp
creation_rules:
- pgp: >-
E9FA8C3--CHANGE-WITH-YOUR-PUBLIC-KEY--CDBF,
E9FA8C3--OTHER-PUBLIC-KEY--CDBFE9FA8C3C96F
Lets encrypt it
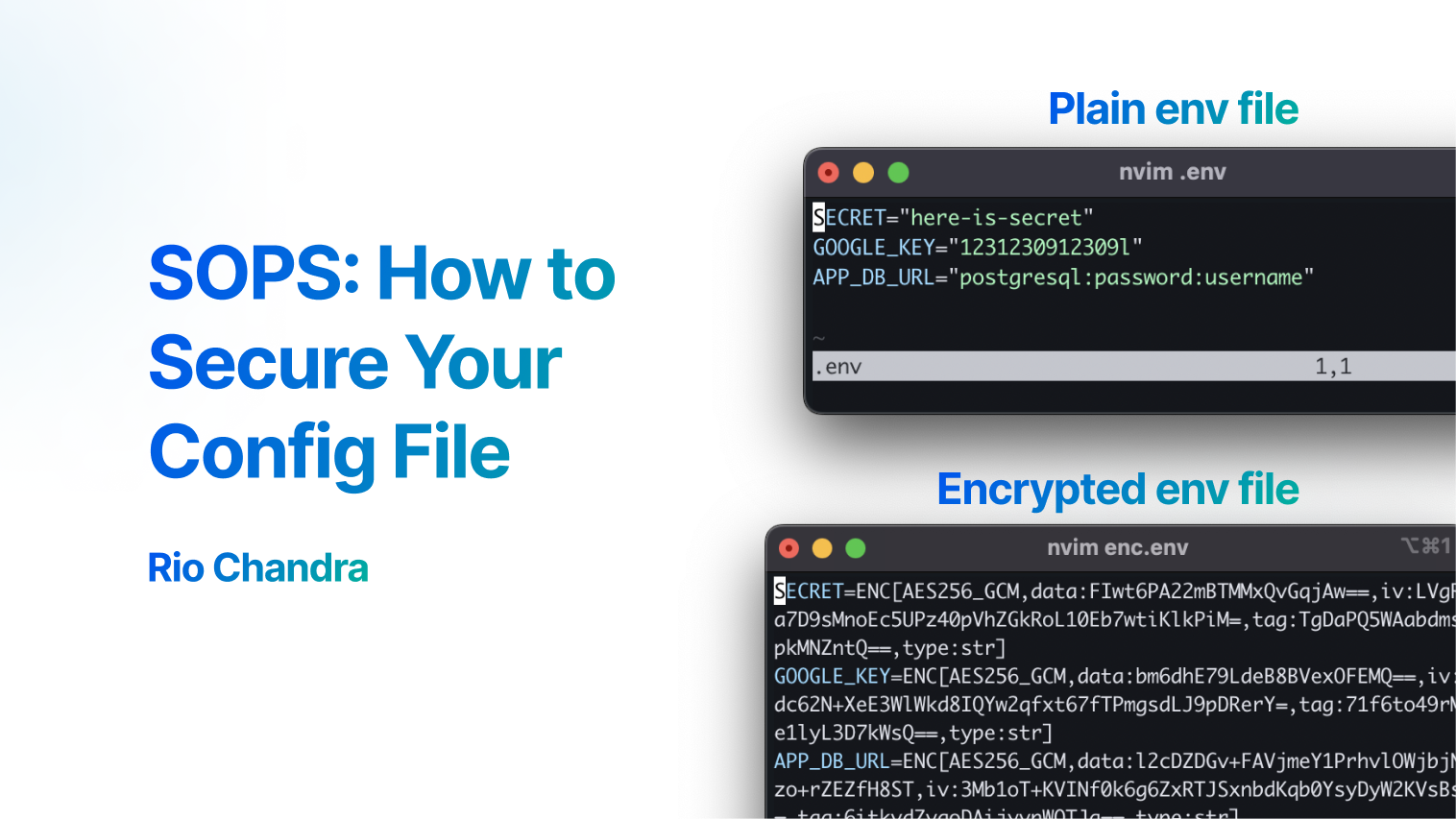
For example, your .env file looks like this:
SECRET="here-is-secret"
GOOGLE_KEY="1231230912309l"
APP_DB_URL="postgresql:password:username"
Encrypt file .env using sops and save it into enc.env file, you can change the name of the file.
Note: SOPS detect file format! we keep the *.env format at the end of file.
sops -e .env > enc.env
You will see enc.env generated like this:
SECRET=ENC[AES256_GCM,data:RqwDRwGwT+GTJJcsmmz+ZA==,iv:Y10UfZ46UBC5YggdzSu2Qnks+QqC/J9rp03S9BFHEjI=,tag:S8pc+AB5hvq/3l/AjRFkBA==,type:str]
GOOGLE_KEY=ENC[AES256_GCM,data:q......6BWPg==,type:str]
APP_DB_URL=ENC[AES256_GCM,data:2khdgs......H3E+zhQbkNeN,iv:nk0v+gv23w1UJwkWSbSs1ff95HPZicTtKIZ1L6zSywM=,tag:CI5UmEfixoVqU44jhgCY+w==,type:str]
sops_lastmodified=2024-08-11T09:39:10Z
sops_mac=ENC[AES256_GCM,da......kKAWk=,iv:vayP/sdn8dPyfDmnae22WwMPp7URymYeX/dQWxQzl6s=,tag:5pbP1hPlwhHuEqcZy/iiAw==,type:str]
sops_pgp__list_0__map_created_at=2024-08-11T09:39:10Z
sops_pgp__list_0__map_enc=-----BEGIN PGP MESSAGE-----\n\nhQEMAwmb.........E7XnSOUw4HFYQ==\n=B0hJ\n-----END PGP MESSAGE-----
sops_pgp__list_0__map_fp=E9FA8C3C96FE003FF38FD7552459B2802BA5CDBF
sops_unencrypted_suffix=_unencrypted
sops_version=3.8.1
All values are encrypted, only key visible. This make SOPS special, it left the key unencrypted so we know what data inside them without knowing sensitive data.
Decrypt now
Decrypt file enc.env using this command
$ sops -d enc.env > .env
# Or
$ sops enc.env > .env
You can run this command inside your server to install into your application
Alternative
Is there any alternative for this? yes, there is git-crypt. It will encrypt the whole repository and decrypt the files when pulling. This alternative is good if you consider to use different repostiory to store env or configuration file.
When NOT use SOPS
Simple application may not require this but still you SHOULD NOT put env or configuration file inside your git repository, maybe you have other method to transfer env configuration from your local to your server. Copy and paste key is the fastest way to setup configuration file into application.
Conclusion
Configure, share and manage env configuration always become tedious work. Share to other developer also always have risk the key maybe leak. Send sensitive data on internet always makes system insecure. Asymmetric Encryption is a good way to keep data sensitive hide inside public internet, encryption using public key and decryption using secret key. SOPS using this method to secure the configuration file. You can read full information about SOPS on their repository.
If you like this article please follow and stay tuned. See you in next article

Leave a Reply